Spanning Tree in a particual NW architecture
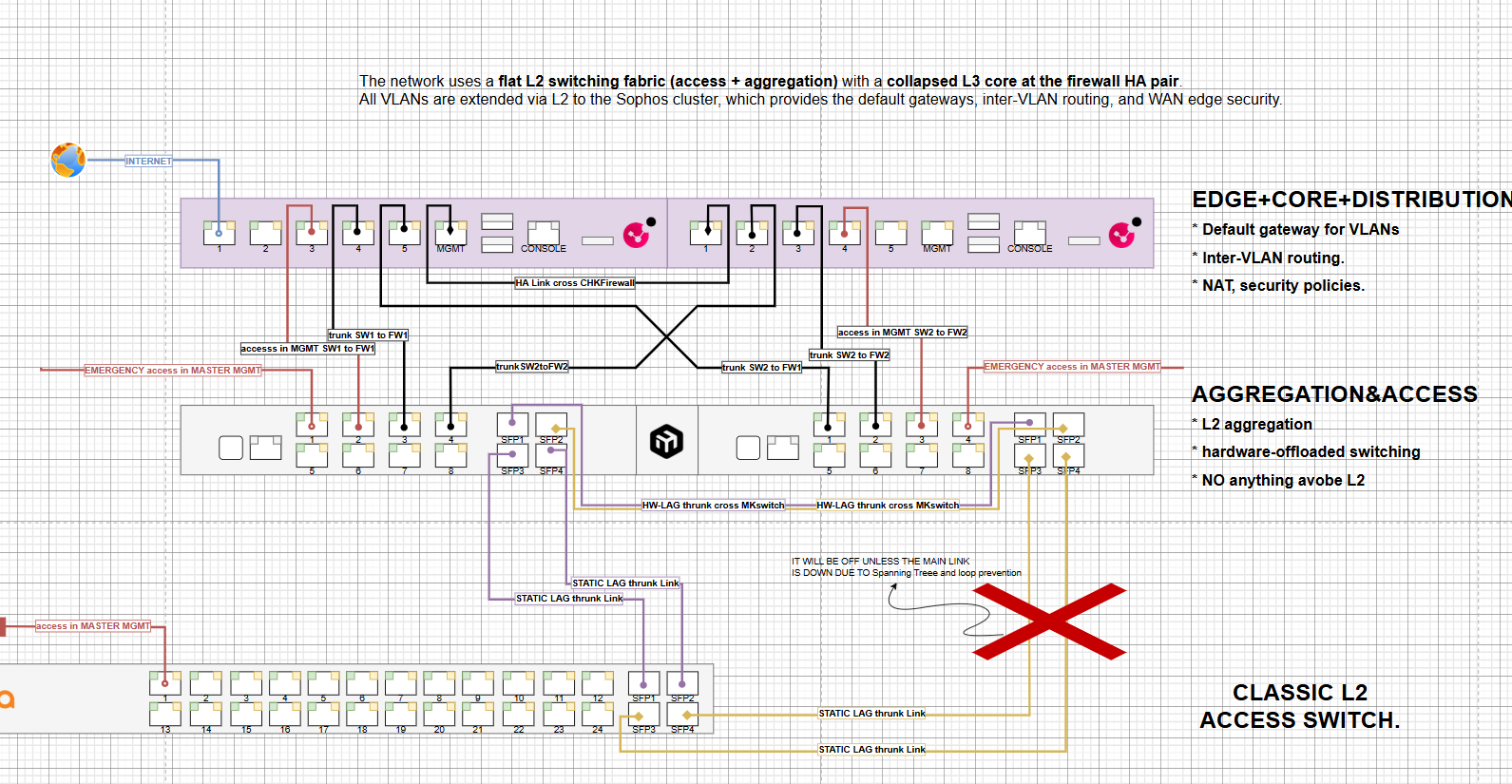
Today I went back to working on the architecture of the infrastructure I want to build in my homelab, and I was discussing the configuration in the Homelab Discord to understand whether I was doing something wrong, since it’s not a super standard setup.
Someone told me that I should run STP directly on the firewalls as well, so everything would be in order and I wouldn’t risk loops.
However, since I wasn’t planning to aggregate links from the firewalls to the switches, and I wasn’t planning to bridge ports, I told him that in theory I shouldn’t have any loop issues.
He replied that yes, that’s correct, but at the same time he dismissed the reason why I arranged the interfaces in a “butterfly” layout, adding:
"it's generally there for protecting yourself against link failures purely at L2
I'd prefer not having my STP reconverge on top of a firewall failover
Losing an entire firewall from a switch failure is not ideal either, but at least it's cleaner
Also if you're doing interface checks and you lose a switch that's going to be interesting"
The part where he talks about “losing a firewall from a switch failure” refers to an older message where he said that, in his opinion, it’s less complicated to have
FW1 <-> SW1 and FW2 <-> SW2
without the butterfly links.
But to me that’s kind of nonsense and a secondary concern: I don’t think I should have any issues not doing bridging in the architecture I had in mind.
Maybe there’s something I’m missing, but I don’t know, I think that without bridges I avoid loops, and in theory I don’t lose redundancy since I already have LAGs with Spanning Tree between the switches (so with one of the two firewall links I can still reach everything).
Someone told me that I should run STP directly on the firewalls as well, so everything would be in order and I wouldn’t risk loops.
However, since I wasn’t planning to aggregate links from the firewalls to the switches, and I wasn’t planning to bridge ports, I told him that in theory I shouldn’t have any loop issues.
He replied that yes, that’s correct, but at the same time he dismissed the reason why I arranged the interfaces in a “butterfly” layout, adding:
"it's generally there for protecting yourself against link failures purely at L2
I'd prefer not having my STP reconverge on top of a firewall failover
Losing an entire firewall from a switch failure is not ideal either, but at least it's cleaner
Also if you're doing interface checks and you lose a switch that's going to be interesting"
The part where he talks about “losing a firewall from a switch failure” refers to an older message where he said that, in his opinion, it’s less complicated to have
FW1 <-> SW1 and FW2 <-> SW2
without the butterfly links.
But to me that’s kind of nonsense and a secondary concern: I don’t think I should have any issues not doing bridging in the architecture I had in mind.
Maybe there’s something I’m missing, but I don’t know, I think that without bridges I avoid loops, and in theory I don’t lose redundancy since I already have LAGs with Spanning Tree between the switches (so with one of the two firewall links I can still reach everything).