'Comet AI' Discord quest
I installed the Comet AI browser from the Discord quests, but I searched it online and some sources said it scraps data from my PC and uses it to help develop its AI. Does anyone know if this is true? And if it is, what steps should I take to remove it? I've uninstalled the main application off my PC (I use an iMac with macOS) and I before deleting it, I didn't agree to the terms of service and privacy policy. All I've done is installed it, let it run on the start screen for 15 min, move the 'Co...
is anyone here familiar with GOAD lab setup?
i need help setting up this lab environment. i would really appreciate the help, thanks so much.
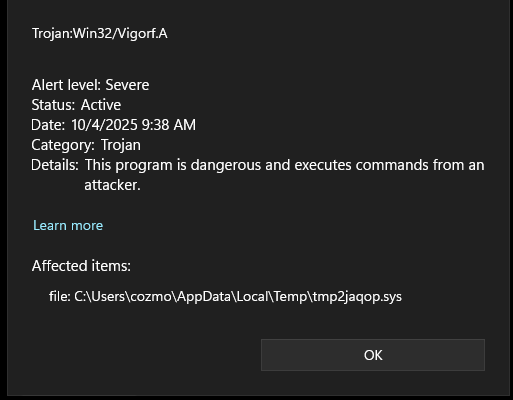
Defender keeps flagging .tmp files.
This morning I turn on my computer and Windows Defender keeps flagging temporary files in the temp folder. I tried removing the whole directory adn the apps could just re add their files. But now they're coming back and the list is growing. I tried to use Avast because it was the first thing I could download but it didn't flag anything. Can anyone help me out? Thanks!
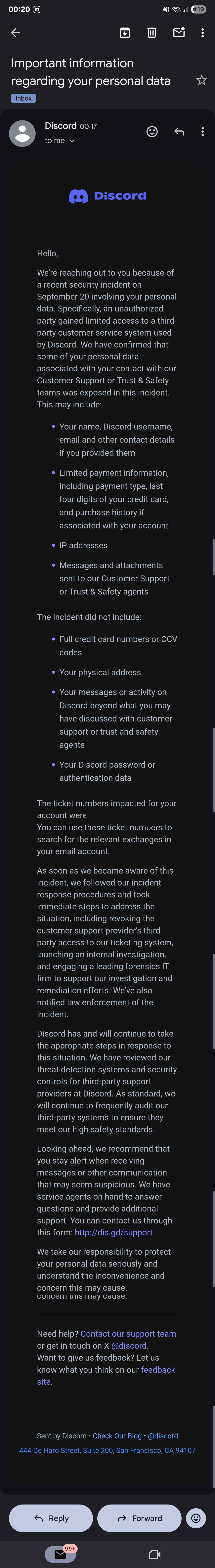
Discord Security incident
A friend of mine recieved the same email at roughly the same time as well. Is this legit?
Cyber Club Topic Recommendations
Hello all, I have a high chance of leading a cybersecurity club (about to find out approval in around 3-4 hours) and was wondering what are some of the topics I should teach?
I was thinking of exploring the privacy and security of apps and how they all work, for example how the tor network works, tails os, metadata on images, but I’m open to ideas on what else I could teach or do within the club
I would love a team CTF but I would need to keep it beginner friendly and by CTF’s nature it may be confusing to them...
General Support for CyberSecurity
Hey everyone, I was wondering I completed the THM Cyber 101 and received my certification. It is 15$ a month and as a person in Iran which one dollar costs about 115,000 Toman, it is really hard to pay the price.
Is there a way I can continue my journey and still learn without paying for tutorials? I feel like I still have a lot more to learn in this field....
Questions to get started?
me is just getting started (me is 17) it is early, because me is doing a College In The High School program, and my overall degree will be Computer Sciences hope to go into cybersecurity or security architect, things like that.
so my high school program that has coding and stuff and me struggles (not good with coding) and we want to code stuff on here for my server.
What platform to use and what does me need to download to get more into everything?...
Somethings up with my ram
Hi, ive noticed recently even after i wiped my pc that I'm always using 10 gigs of ram even with only 1 light task running. Can anyone help?
Not sure if this classifies as tech
Buddy wants a big file organized to notion, was wondering if there’s a quicker way to add a page, title and add the info instead of manually doing it all. Will be able to send video below (maybe?)
Malicious discord gift?
A buddy of mine showed me this discord gift link he was sent. He believed it was malicious but him nor I really know.
I tried running it through a few url scanners but it just says its safe(but gives the link to discord.com/promotions which is officially discord but im sure it wouldn't be hard for someone to fake it)
If anyone has any ideas or input it would be greatly appreciated as im completely lost
...
Unity Engine not Launching error
Hey Everyone . Hope every thing alright
I want to do game dev and my PC specs are
i7 6700
HP 802-F
16gb ram 2200 mghz (No Gpu)...
screen partially black.
sooo i was on a peaceful walk outside, got back home to my pc just to see the screen got a black spot on the right. it can still display but it's a lot darker than the rest of the screen.
it's a very old aoc e2043Fs btw....

Opinions on my project
I need to create an ai ml realtime phising detector
i have created it somehow, but i need some opinions from others as to how it is.
leaving the front end aside as its shit, can someone help me with this.
we join a vc and ill screen share, if its possible?...
My chrome keeps freezing
Hello, for some reason almost everyday when I leave chrome open for a while without using it, when I actually need to use it its either frozen or jsut blacked out and this has been happeneg for a week now. Now this is in my school computer so not sure if something the school installed has something to do with that. All help will be appreciated, Thx!
My pc was acting weird.
So yesterday when I turned on my pc and just started using it, i noticed that it was rlly laggy and i got a lot of stutters. I checked wit defender and didn't find anything, but when i went to open my task manager, my pc just restarted out of nowhere. After this I wiped my drive, should I be fine?
PC Not starting properly
Hello I restarted my PC a few days ago after installing a driver for something and to update it. It goes to a black screen with a loading symbol on the bottom but no windows logo. I got it into recovery mode several times to try some stuff from yt but nothing worked. I then went back to the loading screen and left it there, and after a while it was just a black screen with a mouse. I leave it like that but nothing happens, so I restart it again and ever since its just been booting into recovery...