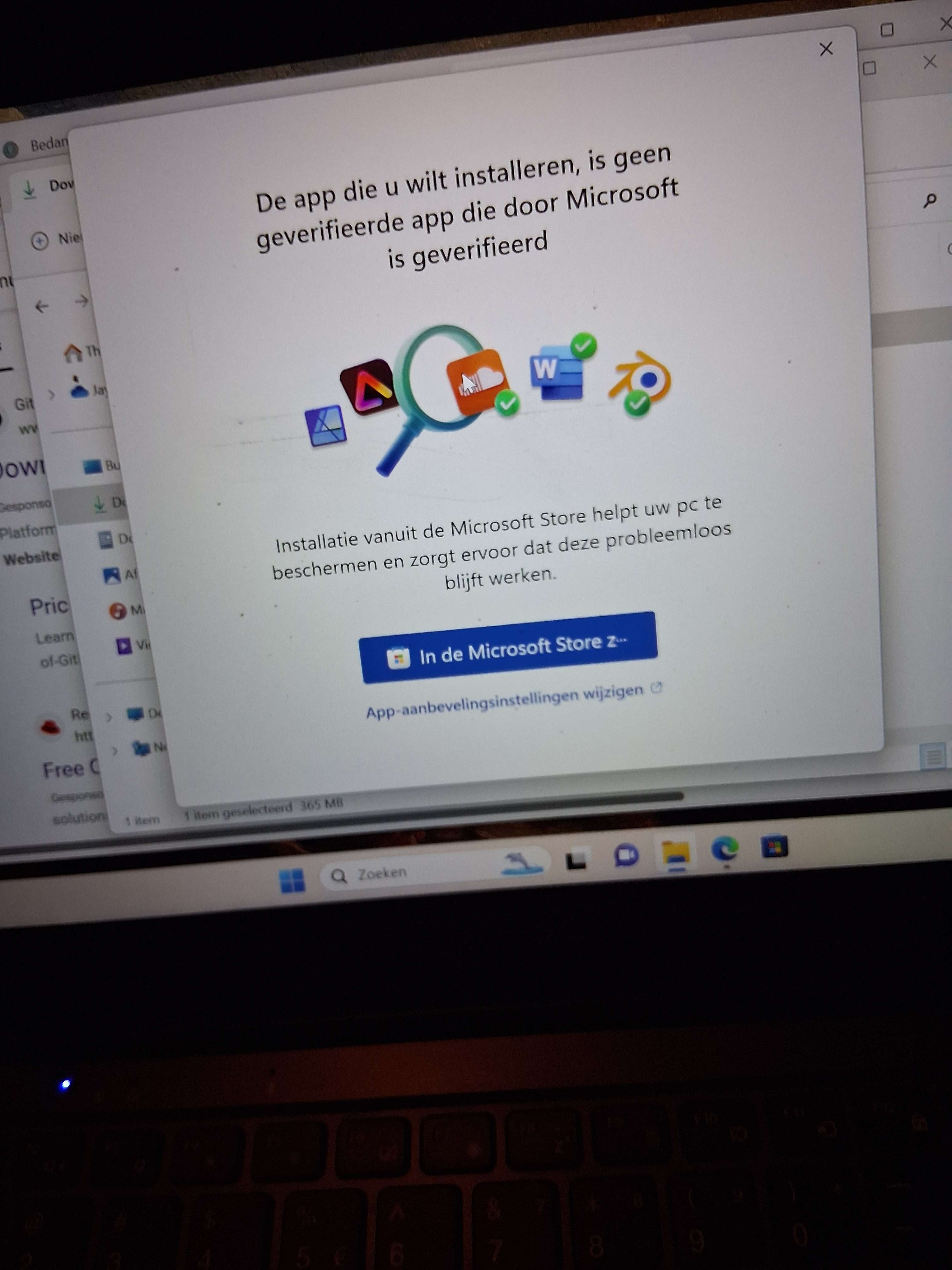
PC Not starting properly
Hello I restarted my PC a few days ago after installing a driver for something and to update it. It goes to a black screen with a loading symbol on the bottom but no windows logo. I got it into recovery mode several times to try some stuff from yt but nothing worked. I then went back to the loading screen and left it there, and after a while it was just a black screen with a mouse. I leave it like that but nothing happens, so I restart it again and ever since its just been booting into recovery...
Linux installation
hey guy im new at cybersecurity stuff and i want to install linux to get to know the system, which type of linux should I install, most of the people tell me Kali Linux, but if anyone have any other suggestions i would be very grateful
Factory reset
Hello so yesterday I installed malware on my pc I think it’s a rat or any other malware idk but then I factory resetted my pc with cloud download and remove everything and clean data option can it come back and reinfect the system or Is it very rare from what I heard ?
Cybersecurity
Hey, everyone, can you please guide me, I am not a hacker, just a concern person with zero knowledge of coding. I work in school, and just recently we have encountered the Cyberbullying and online harrasment. Someone has started an ig page where inappropriate stuff about these staff is been posted on this page we have already requested the state cybersecurity unit, the second time and there is still no positive response. What can we do?
Windows defender flagging and quarantining lots of files I don't have as severe and high.
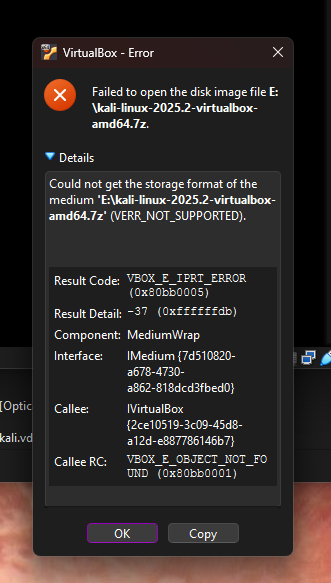
I installed Kali Linux on VirtualBox 2 days ago to play with Metasploit and other tools but never did anything serious. Are these the VM files or am I getting hacked?
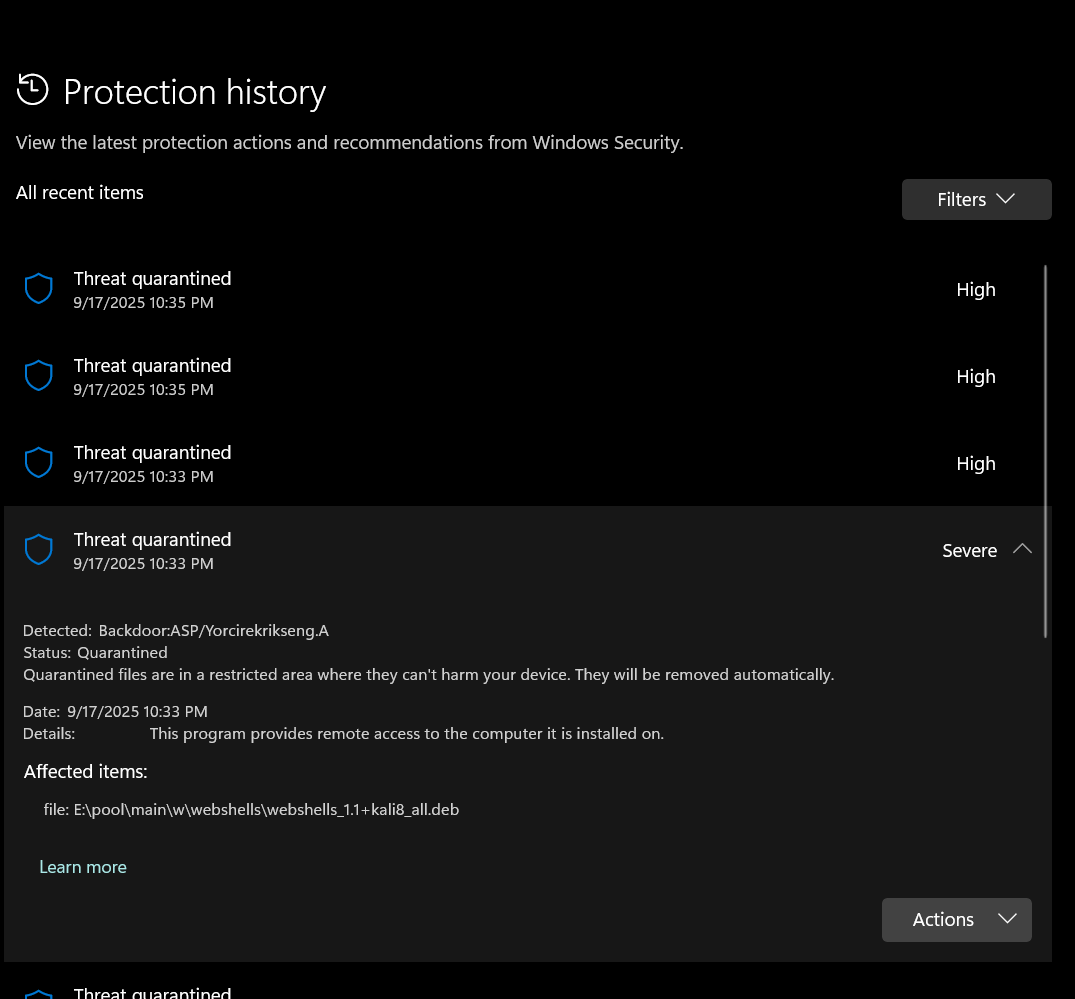
Account help
So i have an discord account that has someone in it, changed passwords and hes still in sending crypto shit, 2FA, again, how do i stop him (i have access to the account)
OSINT CTF
I am in a CTF and it is really confusing we have this image,and we should try and guess where this is from... we have this description to complete the image:
Having set out into the world, the elder brother stopped in a kingdom where he proclaimed himself king. When word spread through the land about the so-called new king, the whole people rose in revolt. A narcissistic herald, angered by the intruder’s deed, swore never, for as long as he lived, to set foot on the land touched by the so called king. And one day, as he pondered how to gain recognition from the heralds of the south, the north, and the east, he decided to name his fortress in his own honor. Said and done. He hung the coats of arms of all the houses in his fortress, but among all these houses, only one stood out: the house whose emblem bore three red beads.
Does anyone atleast know a program that can complete the burnt banner?...

vmware installation in win11
i am getting a popup saying vmware cant be installed cause hyper v is there in this os
Linux distro recomendation
Hello does any1 have some linux distro recomendation cause arch haved kind of becomed boring for me
Help on how to blog securely on my portfolio showing things without getting crushed? ;)
Hey guys!
I recently did my portfolio website and I created my blog section in which I want to share you know some labs I do, CTF etc...
But the issue is that there are some things I cant share online like that, for example how would I blog a wifi password cracking (that I did with my wifi) using aircrackng? I cant share the whole process because there is sensitive info you know what I mean?
How would or how do you guys do?...
My new A50 X headset will not recognize on my PC, PLEASE HELP
Hi, I just bought the logitech A50 X gaming headset and for some reason it wont recognize on my PC, this has also happened with 2 previous steelseries headsets, i spent the money and i really dont wanna go through refunding it, ive tried force updating the drivers to make it recognize the headset. redownloading/updating all of my pc's drivers and a few other things, PLEASE HELP!! thank you and have a good day
My laptop isnt booting up
Hi everyone this is my laptop i m trying to boot up it has no physical damage no misuse i use it for art the screen is turning on but it is black
My laptop isnt booting up
Hi everyone this is my laptop i m trying to boot up it has no physical damage no misuse i use it for art the screen is turning on but it is black
urgent help, i need to control my phone using my pc
i have broken my phone really badly yesterday, not that it doesn't work anymore, but the screen is all messed up and it touches random places, i need an application that i can use to control my phone or backup important files, if that's possible without having to install anything on my phone (i can unlock it)
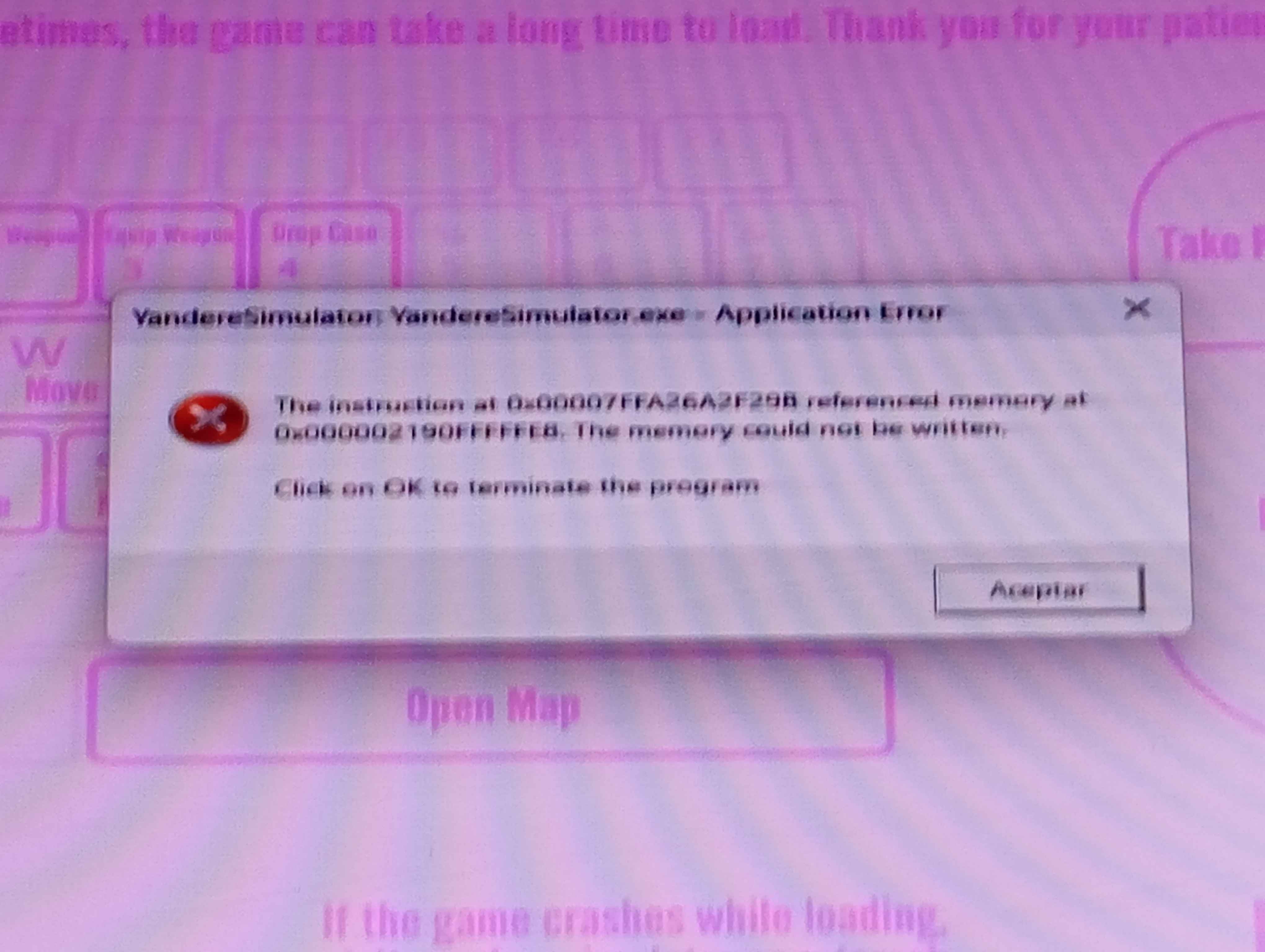
im as smart as a chair
i tried playing sum and this message popped up. I looked up what to do but since yt removed dislikes a while ago i cant tell what tutorial works and what doesnt just with it. I tried doing some called "scannow" or wtv and it said my computer had a bunch of non solved issues but couldnt do anything about it
Solution:
oh i have a solution for you, don't play yandere simulator
its urgent and much complicated to explain in texts . i need someone who knows about pc . i will sho
come in vc and i will share my screen